Bitcoin network
By Wikipedia,
the free encyclopedia
https://en.wikipedia.org/wiki/Bitcoin_network
Advertisements:
The bitcoin network is a peer-to-peer payment network that operates on a cryptographic protocol. Users send bitcoins, the units of currency, by broadcastingdigitally signed messages to the network using bitcoin wallet software. Transactions are recorded into a distributed, replicated public database known as the block chain, with consensus achieved by a proof-of-work system called «mining». The block chain is distributed internationally using peer-to-peer filesharing technology similar to BitTorrent. The protocol was designed in 2008 and released in 2009 as open source software by «Satoshi Nakamoto», the name or pseudonym of the original developer/developer group.
The network timestamps transactions by including them in blocks that link to form a chain called the block chain. Such blocks cannot be changed without redoing thework that created each block down the chain from the modified block. The chain serves as proof of the sequence of events and that this sequence was verified by a majority of the bitcoin network’s computing power. As long as a majority of computing power is controlled by nodes that are not cooperating to attack the network, they will outpace attackers. This provides a means of providing security not found in other protocols.
The network requires minimal structure to share transactions. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will. Upon reconnection, a node downloads and verifies new blocks from other nodes to complete its local copy of the block chain.
Transactions
A transaction is data with a confirming digital signature. It is sent to the bitcoin network and combined with others to form blocks. It typically contains references to prior transactions and associates a certain number of bitcoins with one or several bitcoin addresses (public keys). It is not encrypted because the bitcoin system does not hold confidential/private data. A block chain browser combines transactions into a block and adds it to the chain. They can be found and verified. This is necessary to determine technical transaction parameters as well as verify payment details.
A bitcoin is defined by a sequence of digitally signed transactions that began with the bitcoin’s creation as a block reward. The owner of a bitcoin transfers it by digitally signing it over to the next owner using a bitcoin transaction, much like endorsing a traditional bank check. A payee can examine each previous transaction to verify the chain of ownership. Unlike traditional check endorsements, bitcoin transactions are irreversible, which eliminates risk of chargeback fraud.
A bitcoin is a tradeable currency object. Transactions can also be denominated in fractions of a bitcoin, or in multiple bitcoins. Bitcoins are intended to be fungible, though each has a distinct history.
A diagram of a bitcoin transfer
Although it is possible to handle bitcoins individually, it would be unwieldy to require a separate transaction for every bitcoin in a transaction. Transactions are therefore allowed to contain multiple inputs and outputs, allowing bitcoins to be split and combined. Common transactions will have either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and one or two outputs: one for the payment, and one returning the change, if any, to the sender. Any difference between the total input and output amounts of a transaction goes to miners as a transaction fee.
Transaction confirmation
Transaction confirmation is needed to prevent double spending of the same money.
After a transaction is broadcast to the bitcoin network, it is included in a block that itself is published to the network. When that happens the transaction has been mined at a «depth» of 1 block (in the block chain). With each subsequent block that is found, the depth is increased by one. To be secure against double spending, a transaction is not considered confirmed until it is a certain number of blocks deep. This feature was introduced to protect the system from a bitcoin owner attempting to repeatedly spend the same bitcoin (double-spending). Inclusion of transaction in the block happens with the process of mining.
The conventional bitcoin client shows a transaction as «unconfirmed» until it is 6 blocks deep. Sites or services can set their own limits on how many blocks are needed to be found to confirm a transaction. The number six was chosen deliberately: it is based on a theory that the probability is low that wrongdoers could amass more than 10% of the network’s hash rate for purposes of transaction falsification and an insignificant risk (lower than 0.1%) is acceptable. For offenders lacking massive computing power, 6 confirmations are an insurmountable obstacle. In turn any party having more than 10% of the network’s computing power would not find it difficult to achieve 6 confirmations in a row, hijacking the
chain. This would require millions of dollars’ of investment. Bitcoins that are distributed by the network for finding a block can only be used after 100 confirmations e.g. 100 discovered blocks. Conventional bitcoin clients display the coins earned for solving a block only after 120 confirmations.
Hashes and signatures
Two consecutive SHA-256 hashes are used for transaction verification. RIPEMD-160 is used after a SHA-256 hash for bitcoin digital signatures or «addresses». A bitcoin address is the hash of an ECDSA public-key, computed as follows:
Key hash = Version concatenated with RIPEMD-160 (SHA-256 (public key))
Checksum = 1st 4 bytes of SHA-256 (SHA-256 (Key hash))
Bitcoin address = Base58Encode (Key hash concatenated with Checksum)
Bitcoin addresses
A bitcoin transaction log showing addresses
A bitcoin address is an identifier (account number), starting with 1 or 3 and containing 27-34 alphanumeric Latin characters (except 0, O, I, l). An address can be also represented as a QR-code, is anonymous, and does not contain information about the owner. It can be obtained for free, using, for example, bitcoin software.
The ability to transact bitcoins without the assistance of a central registry is facilitated in part by the availability of a virtually unlimited supply of unique addresses that can be generated and disposed of as needed. The balance of funds at a particular bitcoin address can be ascertained by looking up the transactions to and from that address in the block chain. All valid transfers of bitcoins from an address are digitally signed using the private keys associated with it.
Private key
A private key in the context of bitcoin is a secret number that allows bitcoins to be spent. Every bitcoin address has a matching private key, which is usually saved in the wallet file of the person who owns the account and can be stored using other means and methods. The private key is mathematically related to the bitcoin address, and is designed so that the bitcoin address can be calculated from the private key but, importantly, the private key cannot be derived from the bitcoin address.
Wallets
Bitcoin users manage their addresses by using a digital wallet. Wallets let users send bitcoins, request payment, calculate the total balance of addresses in use and generate new addresses as needed. Many wallets include precautions to keep private keys secret, for example by encrypting the wallet data with a password or with two-factor authenticated logins.
Bitcoin wallets provide the following functionality:
- Storage of bitcoin addresses and corresponding public/private keys on user’s computer in a wallet.dat file
- Conducting transactions that obtain and transfer bitcoins with or without an Internet connection
- Provide information about the balances at all addresses, prior transactions and spare keys
Bitcoin wallets have been implemented as stand-alone software applications, web applications, printed documents and memorized passphrases.
Software wallets
Software that directly connects to the peer-to-peer bitcoin network includes bitcoind and Bitcoin-Qt, the bitcoind GUI counterpart available for Linux, Windows and Mac OS X. Less resource-intensive wallets have been developed, including mobile apps for iOS and Android devices that display and scan QR codes. These services could be built into a stand-alone hardware device.
Website wallets
Many bitcoin websites provide addresses associated with an online account to hold bitcoin funds on the user’s behalf, similar in ways to bank accounts. Other sites function primarily as real-time markets, facilitating the sale and purchase of bitcoins with other currencies such as US dollars or euros. Users of this kind of wallet are not obliged to download the entire block chain, and can manage their wallet with any device. Some wallets offer additional services. Wallet privacy is provided by the website operator. This «online» option often serves as the introduction to bitcoin for new users and for short-term storage of small sums, such as day-to-day spending. Website wallets are not recommended for storing large amounts of bitcoin because security cannot be absolutely guaranteed online.
Example of a bitcoin paper wallet with private key hidden beneath tamper-evident seals
Paper wallets
Bitcoin address keys may be printed on paper and used to store bitcoins offline. Compared with «hot wallets»—those that are connected to the Internet—these non-digital offline paper wallets are considered a «cold storage» mechanism better suited for safekeeping bitcoins. It is safe to use only if the holder prints the paper themselves. Bitcoins from a «cold storage» record obtained from a second party as a gift or payment should be immediately transferred to a safer account because the private key could have been copied.
Vendors offer banknotes, coins, cards and other physical objects denominated in bitcoins. The bitcoin balance is bound to the private key printed on the banknote or embedded within the coin. Some of these instruments employ a tamper-evident seal that hides the private key. It is generally insecure because the producer of a banknote or a coin cannot guarantee that no copies of the private key exist.
To ensure safety, the following measures are recommended:
- Wallet backup with printing or storing on flash drive without connection to Internet
- Encryption of the wallet
- Using a highly-rated service
Timestamps
The bitcoin specification starts with the concept of a timestamp server. To avoid the need for a trusted third party verifying and timestamping bitcoin transactions, bitcoin timestamping server is distributed. It is based on a proof-of-work scheme using the SHA256 hash function. New transactions are verified and collected to a new block and significant work has to be performed to find the timestamp acceptable for the network (the setup is adjusted so that the whole network needs approximately 10 minutes to find the requisite timestamp). Using the hash function, all blocks are chained together. A potential attacker wanting to change the transaction history would not just need to replace the historical block of interest, but would also need to replace all the subsequent blocks to obtain a longer (in terms of work) chain and outperform all the remaining network nodes continually adding new transaction blocks to the honest chain.
Mining
To form a distributed timestamp server as a peer-to-peer network, bitcoin uses a proof-of-work system similar to Adam Back’s Hashcash and the internet rather than newspaper or Usenet posts. The work in this system is what is often referred to as bitcoin mining.
The mining process involves identifying a value that when hashed twice with SHA-256, begins with a number of zero bits. While the average work required increases exponentially with the number of leading zero bits required, a hash can always be verified by executing a single round of double SHA-256.
For the bitcoin timestamp network, a valid «proof-of-work» is found by incrementing a nonce until a value is found that gives the block’s hash the required number of leading zero bits. Once the hashing has produced a valid result, the block cannot be changed without redoing the work. As later blocks are chained after it, the work to change the block would include redoing the work for each subsequent block.
Majority consensus in bitcoin is represented by the longest chain, which required the greatest amount of effort to produce. If a majority of computing power is controlled by honest nodes, the honest chain will grow fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of that block and all blocks after it and then surpass the work of the honest nodes. The probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.
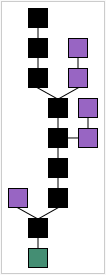
The best chain (black) consists of the longest series of transaction records from the genesis block (green) to the current block or record. Orphaned records (purple) exist outside of the best chain.
To compensate for increasing hardware speed and varying interest in running nodes over time, the difficulty of finding a valid hash is adjusted roughly every two weeks. If blocks are generated too quickly, the difficulty increases and more hashes are required to make a block and to generate new bitcoins.
Bitcoin mining is a competitive endeavor. An «arms race» has been observed through the various hashing technologies that have been used to mine bitcoins: basic CPUs, high-end GPUs common in many gaming computers, FPGAs and ASICs all have been used, each reducing the profitability of the less-specialized technology. Bitcoin-specific ASICs are now available. As bitcoins become more difficult to mine, computer hardware manufacturing companies have seen an increase in sales of high-end products.
Computing power is often bundled together or »pooled» to reduce variance in miner income. Individual mining rigs often have to wait for long periods to confirm a block of transactions and receive payment. In a pool, all participating miners get paid every time a participating server solves a block. This payment is proportional to the amount of work an individual miner contributed to help find that block.
In Cloud mining equipment is hosted in a data center. Mining power is sold for a certain period of time. Cloud mining providers generally use»pooled» mining to to speed payouts.
GPU-based mining rig (click to enlarge)
Lancelot FPGA-based mining board (click to enlarge) 
Avalon ASIC-based mining machine (click to enlarge) 
ASICMINER ASIC-based USB mining device (click to enlarge) 
Several ASICMINER ASIC-based USB mining devices (click to enlarge) 
Butterfly Labs ASIC-based mining machine (click to enlarge) 
A mining farm in Iceland (click to enlarge) Process
A rough overview of the process to mine bitcoins is:
- New transactions are broadcast to all nodes.
- Each miner node collects new transactions into a block.
- Each miner node works on finding a proof-of-work code for its block.
- When a node finds a proof-of-work, it broadcasts the block to all nodes.
- Receiving nodes validate the transactions it holds and accept only if all are valid.
- Nodes express their acceptance by moving to work on the next block, incorporating the hash of the accepted block.
Nodes generally work on extending the longest chain to avoid wasting their efforts. If two nodes broadcast different versions of the next block simultaneously, some nodes receive one before the other. In that case, they work on the first one they receive, but save the other branch in case it becomes longer before they complete their own extension. The tie is broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch switch to the longer one.
Transaction broadcasts do not necessarily reach all nodes. As long as they reach many nodes, however, they will get into a block. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it can request a resend when it receives the next block and realizes it missed one.
Mined bitcoins
By convention, the first transaction in a block is a special transaction that produces new bitcoins owned by the creator of the block. This is the incentive for nodes to support the network. It provides the way to move new bitcoins into circulation.
The continual and steady addition of new coins is analogous to gold miners expending resources to add to gold stocks. In this case, it is computing power (CPU time) and electricity that is expended.
The incentive can be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction. Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and coin creation ends.
Mining versus attacking
The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes (a 51% attack), the attacker would have to choose between using it to defraud people by stealing back their payments, or continuing to use it honestly to generate new coins. The attacker ought to find it more profitable to play by the rules, such rules that favor them with more new coins than everyone else combined, than to undermine the system and the validity of their own wealth.
Local system resources
Once the latest transaction of a coin is buried under enough blocks, fully spent transactions that preceded it can be discarded to save disk space. To facilitate this without breaking the block’s hash, transactions are hashed in a Merkle tree, with only the root included in the block’s hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes need not be stored.
While these calculations are accurate for archived transactions, the load on recent and ‘active’ blocks is significant. The bitcoin network is restricted to a rate of 7 transactions per second, to prevent the network from unsustainable expansion. In comparison, the VISA network handles an average 2,000 transactions per second, with daily bursts of over 4,000 transactions and up to 10,000 during seasonal peaks. If the bitcoin network transaction cap was removed, and the network load was similar to that of VISA’s (2000 TPS), each client (and miner) would require a constant download and upload rate of upwards of 1 megabyte per second, and each 10-minute block would be over 500MB.
Payment verification
Upon receiving a new transaction a node must validate it: in particular, verify that none of the transaction’s inputs have been previously spent. To carry out that check the node needs to access the block chain. Any user who does not trust his network neighbors, should keep a full local copy of the blockchain, so that any input can be verified.
Diagram showing how Bitcoin transactions can be verified
As noted in Nakamoto’s whitepaper, it is possible to verify bitcoin payments without running a full network node (simplified payment verification, SPV). A user only needs a copy of the block headers of the longest chain, which are available by querying network nodes until it is apparent that the longest chain has been obtained. Then, get the Merkle branch linking the transaction to its block. Linking the transaction to a place in the chain demonstrates that a network node has accepted it, and blocks added after it further establish the confirmation.
As such, the verification is reliable as long as honest nodes control the network, but is vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker’s fabricated transactions for as long as the attacker overpowers the network. To protect against this, alerts from network nodes detecting an invalid block prompt the user’s software to download the full block and verify suspect transactions to confirm their inconsistency. Businesses that receive frequent payments generally run their own nodes for more independent security and quicker verification.
Published - March 2016
Text is available under the Creative
Commons Attribution-ShareAlike License; additional terms may apply.
See Terms
of Use for details.
|




